AWS 101: I.A.M. Service every DevOps Novice should know
Getting Started with I.A.M, Users, Groups and Permissions
A.W.S does this seems familiar ? I am sure you must have purchased an item via Amazon or at least visited it once so the term A.W.S. in the recent times is booming in the market and there are several reasons for it. If you are just started with the DevOps I recommend you to have a look on the below links (Just to know what should be going through).
DevOps Terminology Introduction
Introduction to Cloud Providers
The worldwide cloud market is dominated by four cloud service providers: Alibaba in China and Asia-Pacific, and AWS, Microsoft, and Google in other countries.
Smaller cloud services providers are primarily utilised in scenarios that require tailored support for legacy services, or have particular location requirements that the cloud giants cannot fulfil. Overall, the cloud market leaders provide an extensive range of solutions for different use cases by fulfilling the needs of high performance, availability, security and support.
If you are just getting started with the Cloud then the Amazon Web Service (A.W.S.) is a great place to start from as AWS has a great community support and the documentation has greater depths but can be understood easily.
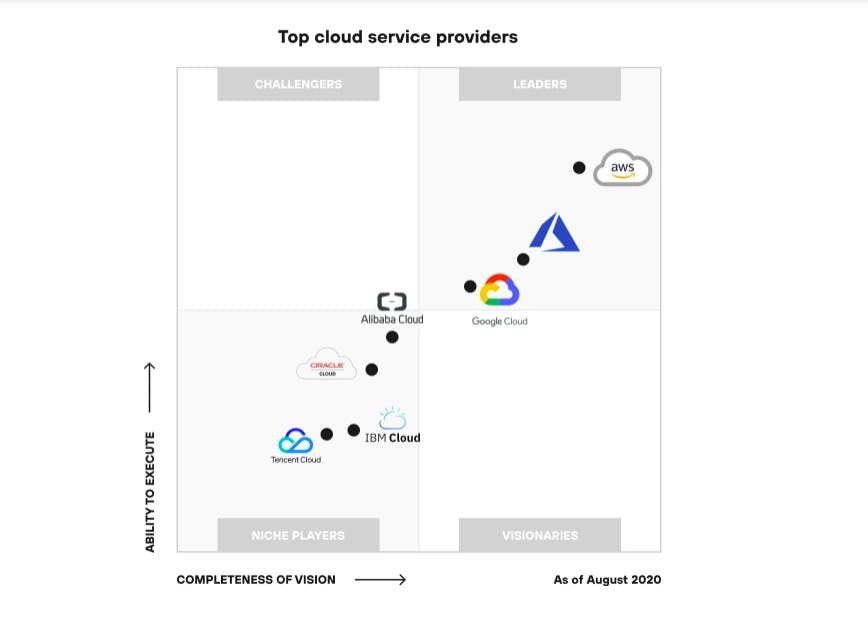
What is AWS ?
A subsidiary of Amazon and founded in 2006, AWS is a leader amongst cloud service providers. It is one of the first cloud computing platforms that became widely available. As you can see from the above graph the AWS is still the market leader in the Cloud Providers Industry.
AWS Services
AWS has over 300+ cloud services for a broad range of use cases and industries. The top Amazon most used services are:
Amazon EC2 (compute cloud),
Amazon RDS (relational database),
Amazon S3 (cloud storage),
Amazon CloudFront (content delivery service)
Amazon Glacier (web storage service).
IAM Introduction
For the first time AWS Users whenever you first try to login it is from the Root User but as you know Root user has all the power to edit update revoke the access to any user and as you know *"with great power comes ..."* you know the rest :'(

In-order to provide t the limited access for all the users, groups there is a service in the AWS known as I.A.M i.e. [Identity and Access Management.]
NOTE: It is always advised to make a new user and we should not work with the root users.
Bookish Definition: AWS Identity and Access Management (IAM), you can specify who or what can access services and resources in AWS, centrally manage fine-grained permissions, and analyze access to refine permissions across AWS.
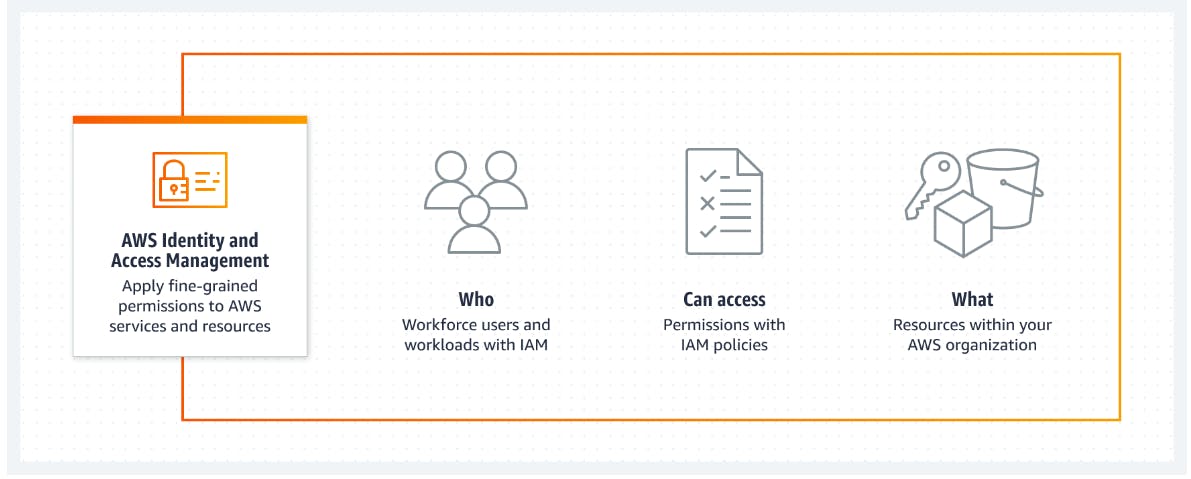
Some important things that you should know about the Groups and Users:
Users they are your company fellows and they can be used to form a group.
The individual user can belong to more than one group and so the access for all that group will also get passed to the users.
Single user can get the policies of different groups and also can get the policies of the root as well.
User should only have the access of which they need they should not have the access to the things that they didn't need to care about.
Now let us gets our hands dirty and try to work on the concepts that we have looked on above.
How to make a user in IAM ?
Note: Its is assumed that user has a root account on the AWS console. (If not get started with it its free.)
Steps to follow
Login via root user.
Search and access IAM service
In Side Nav select the Users from the Access Management Expander.
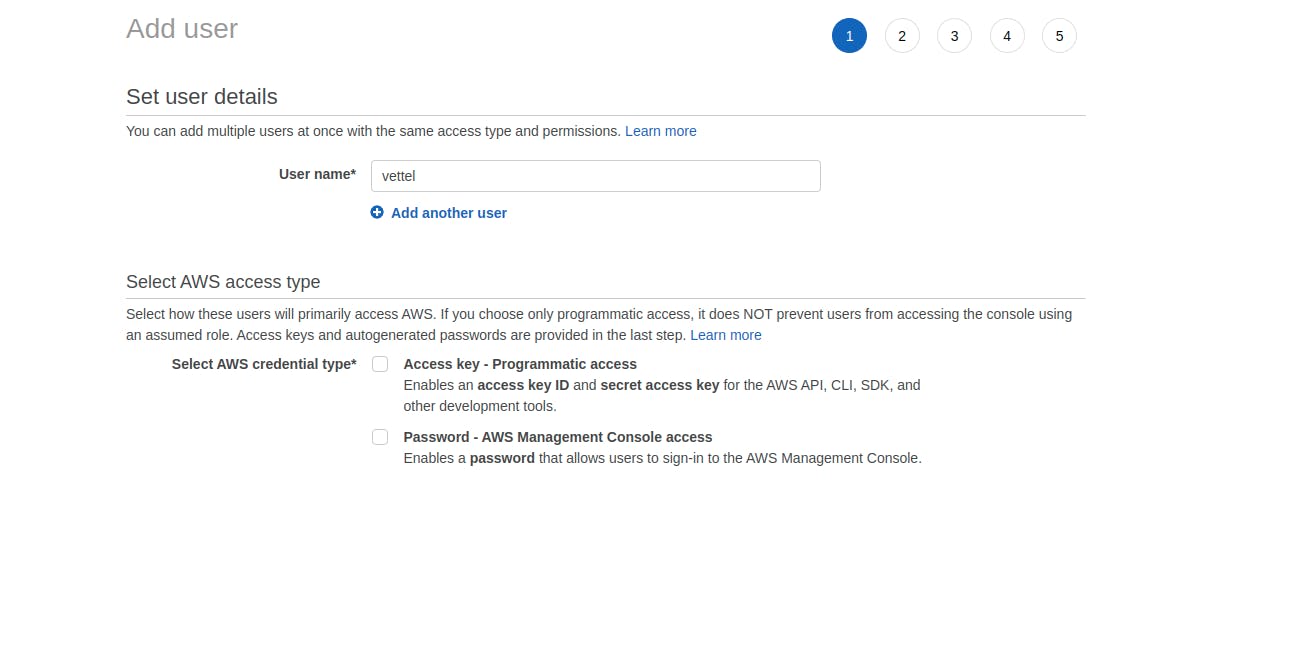
Click on Add Users --> Fill user name (Recommended to add only one user at a time)
- Select the AWS Access Type as --> Password - AWS Management Console access Select the Custom password --> Fill in the field
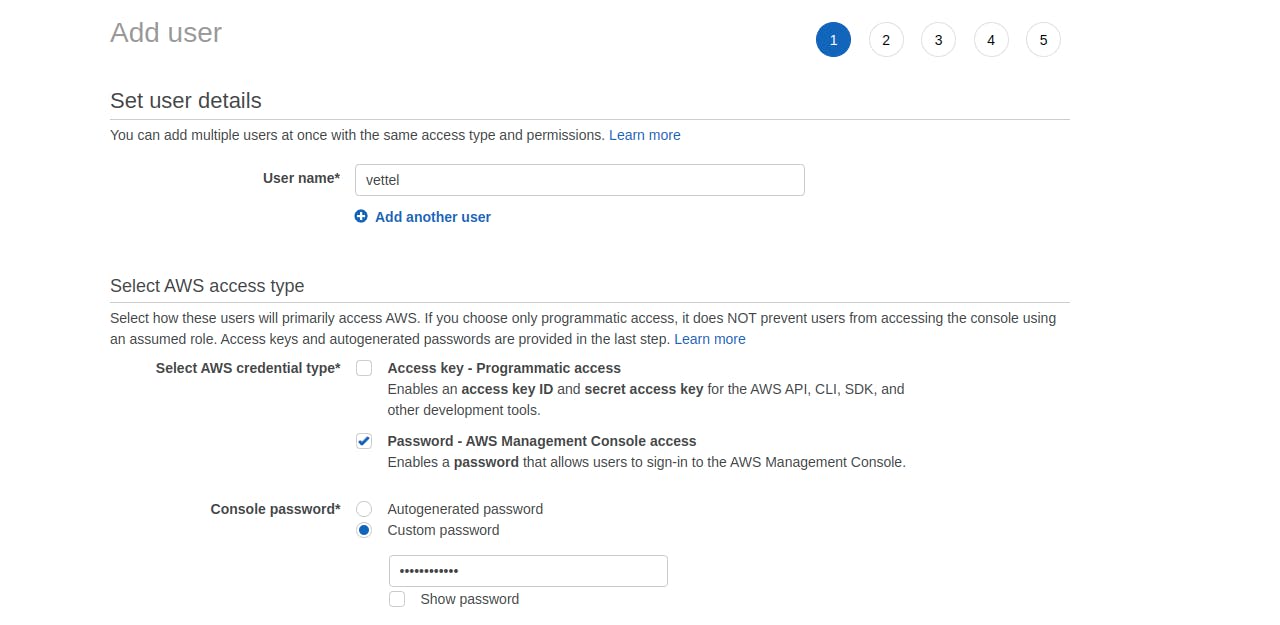
Unchecked the Require Password Reset while next login --> hit next
Add User to group appears --> If we want to add it to a group we can do it now or can also add them later. (For now I will not do that but from the screenshot below you could see that there are certain groups which I had previously created)
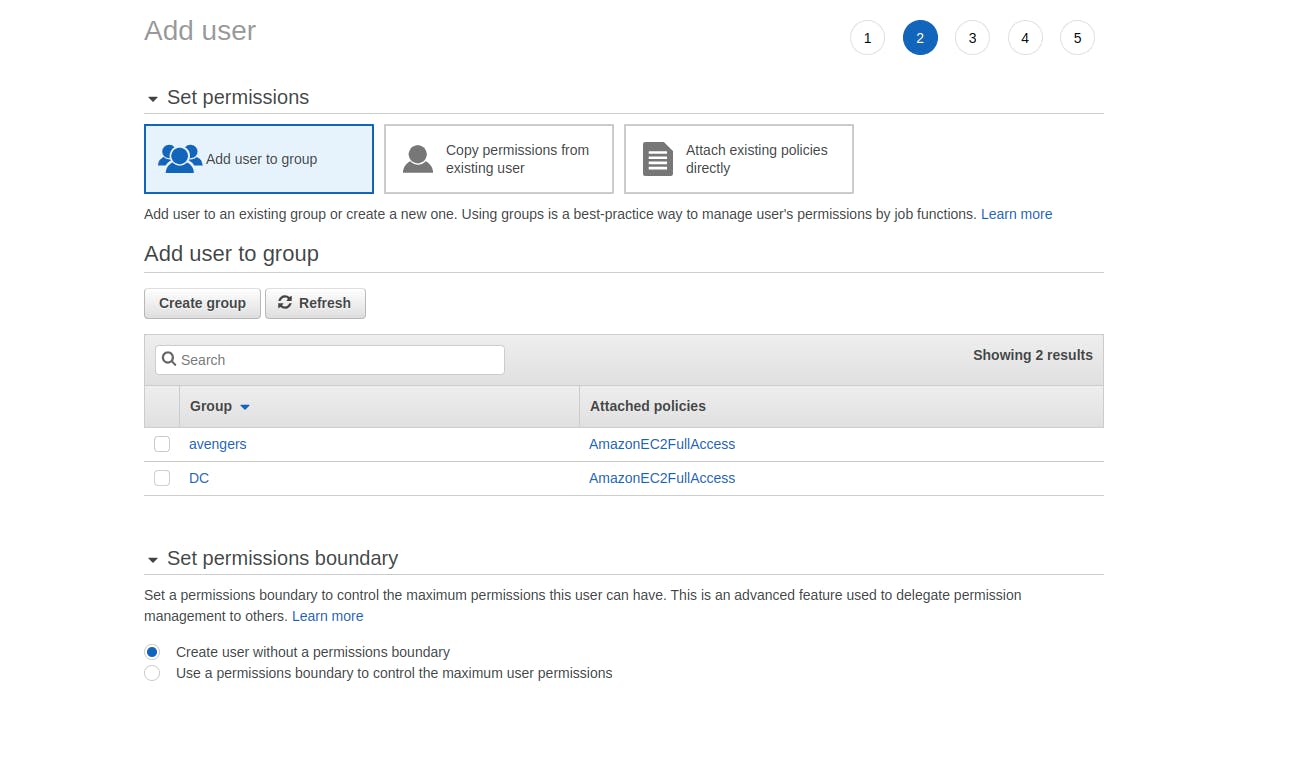
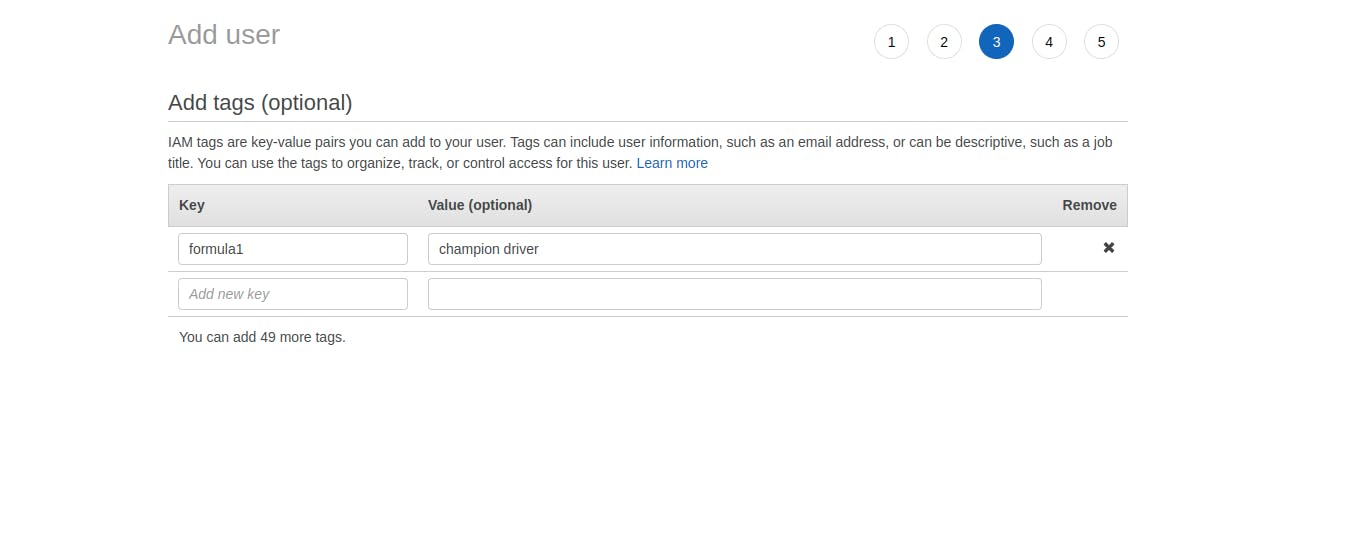
- Select the "Create user without a permissions boundary" in the Set permission boundary--> Move next page Adding a Tags is optional but can be added to remember it further
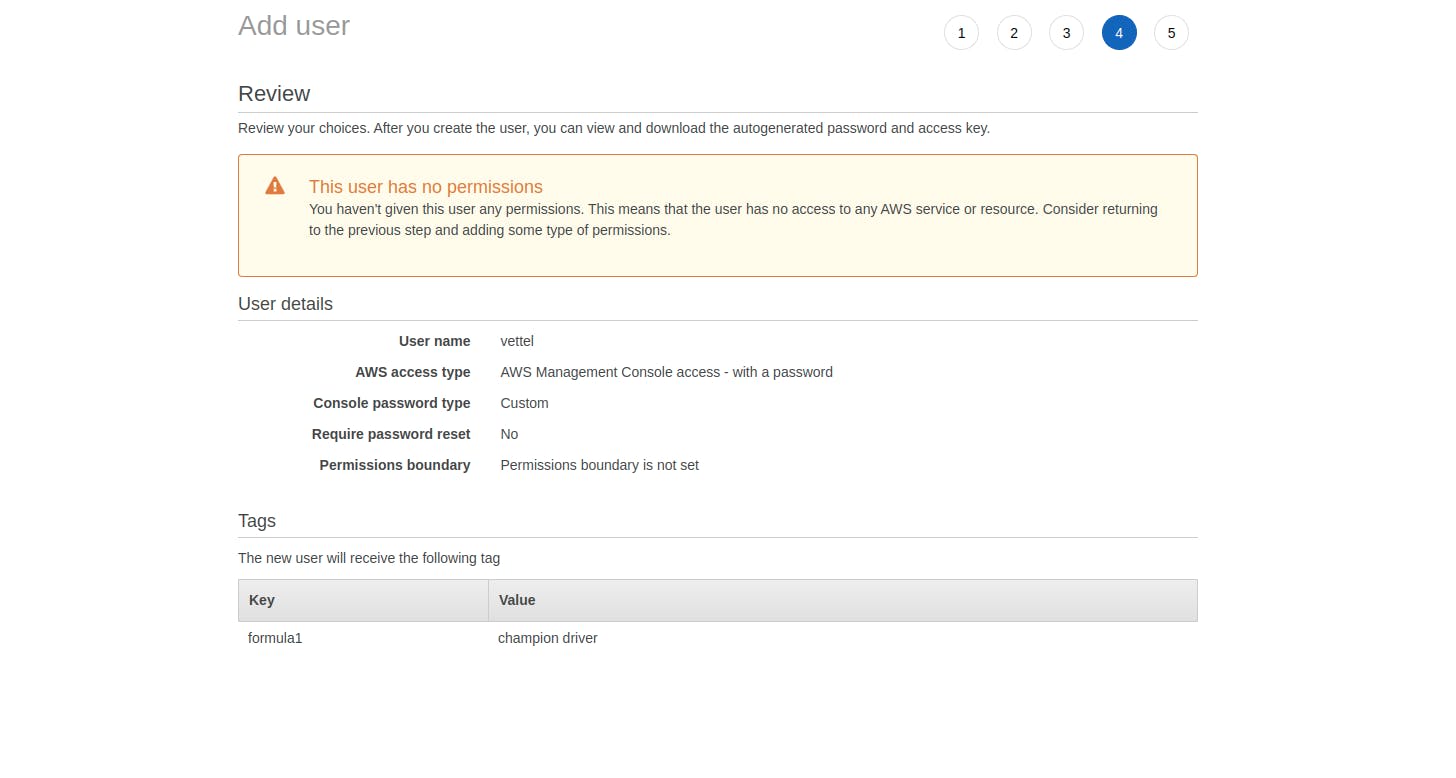
- Now we got onto review page and we can see what are the propeties which we have setted for that particular user --> Hit on Create User (It would give us warning in the console but for now just move on)
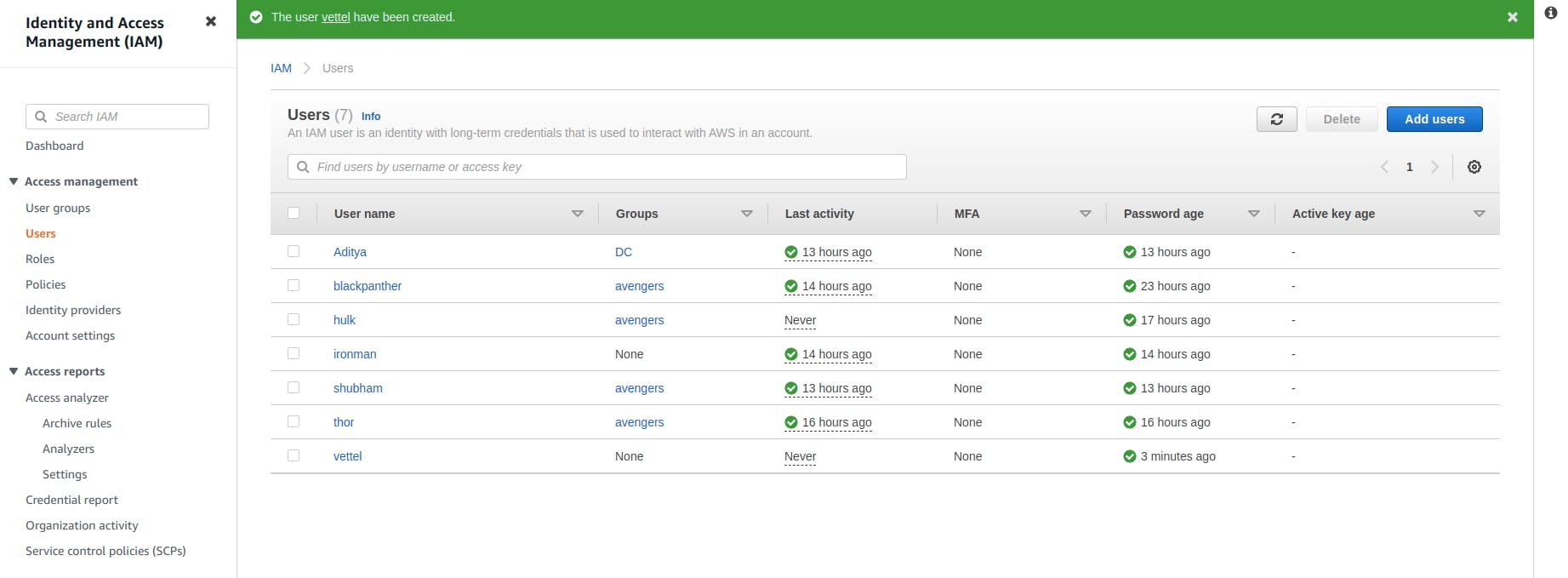
- If all steps are correctly followed then it would show us the Succes dialog message and user is successfully created.
NOTE: Download the CSV file and make sure to keep it safe incase of any backup or discrepancy.
- Checkout the user dashboard you would see the user created
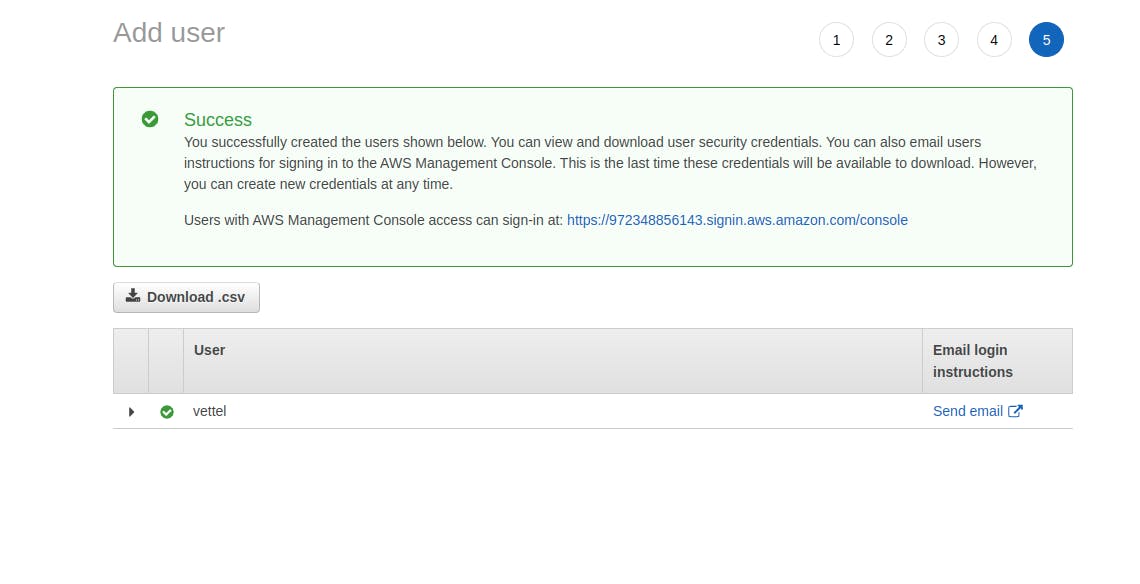
How to add the Permissions to the User ?
Steps to follow
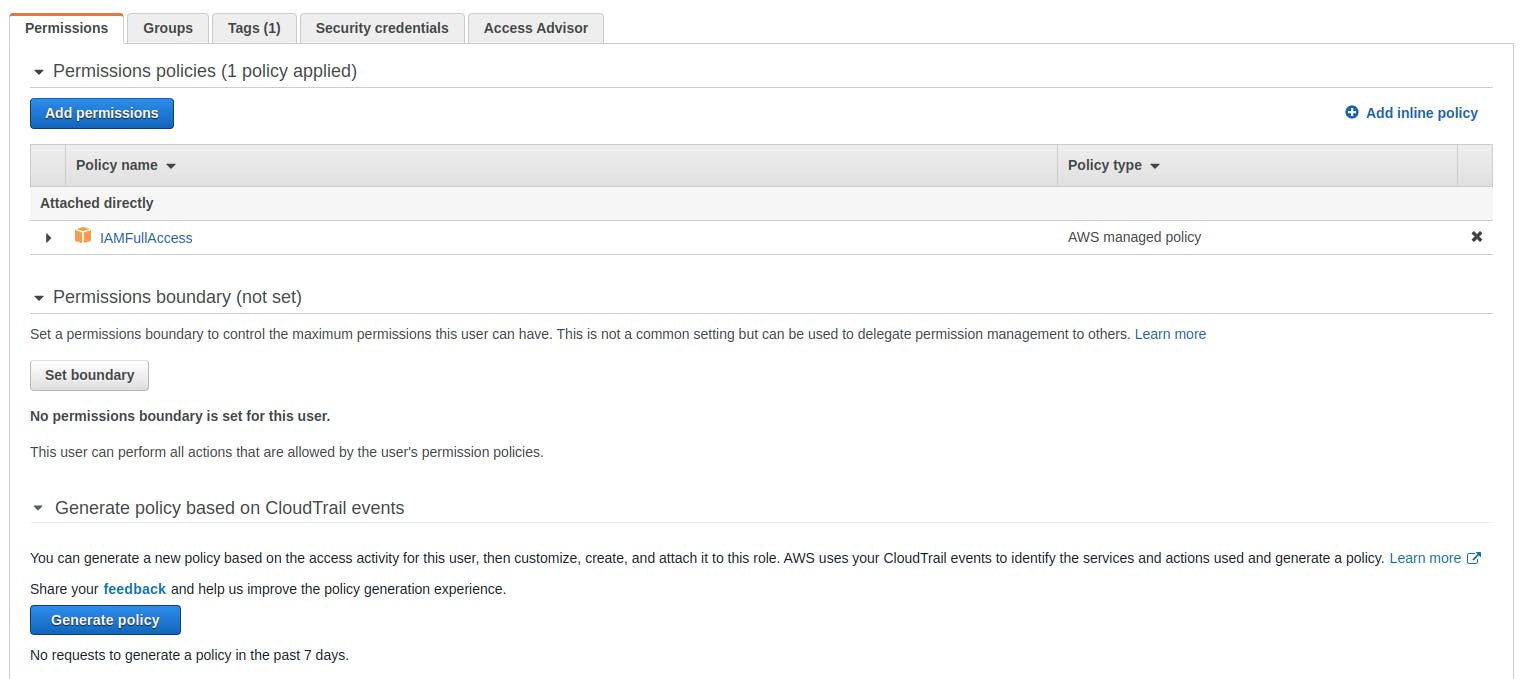
- Click on the user --> Permissions Tab --> Hit on Add Permissions
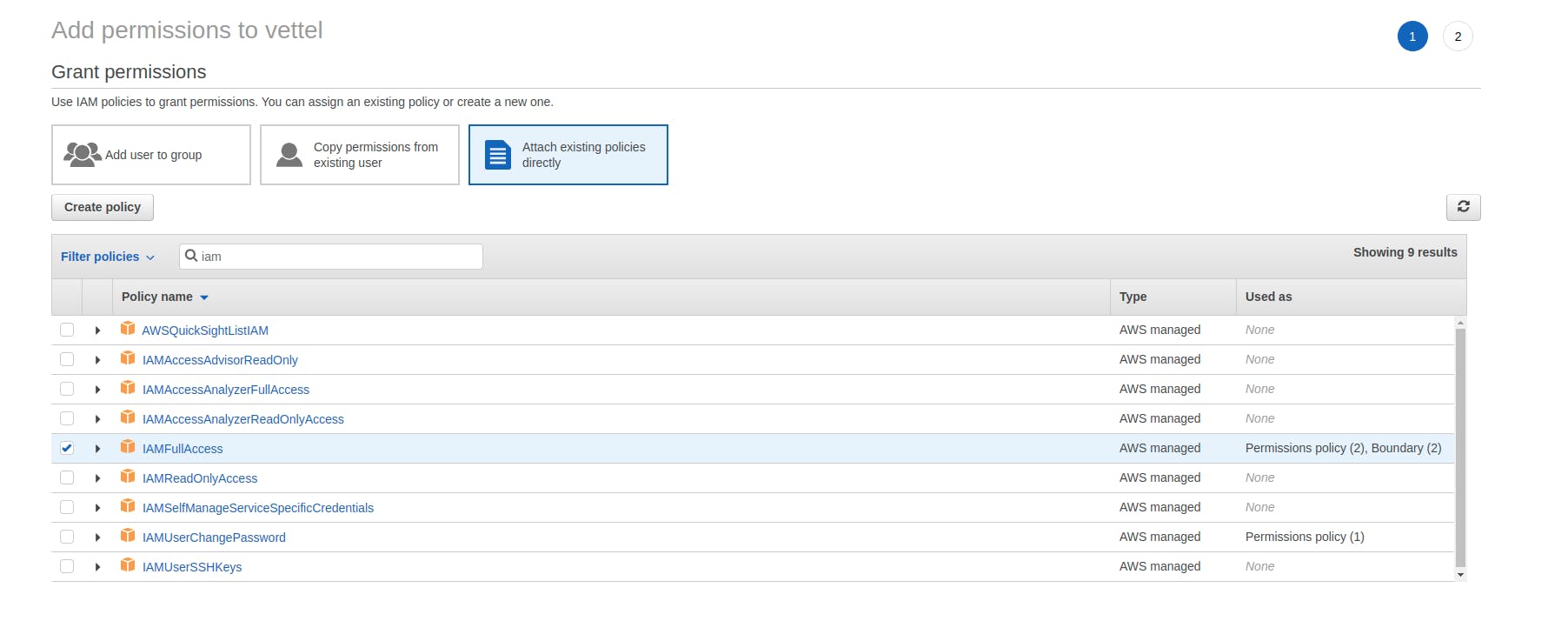
- Click on the "Attach existing policies directly" --> for demo purpose search and add "IAMFullAccess"
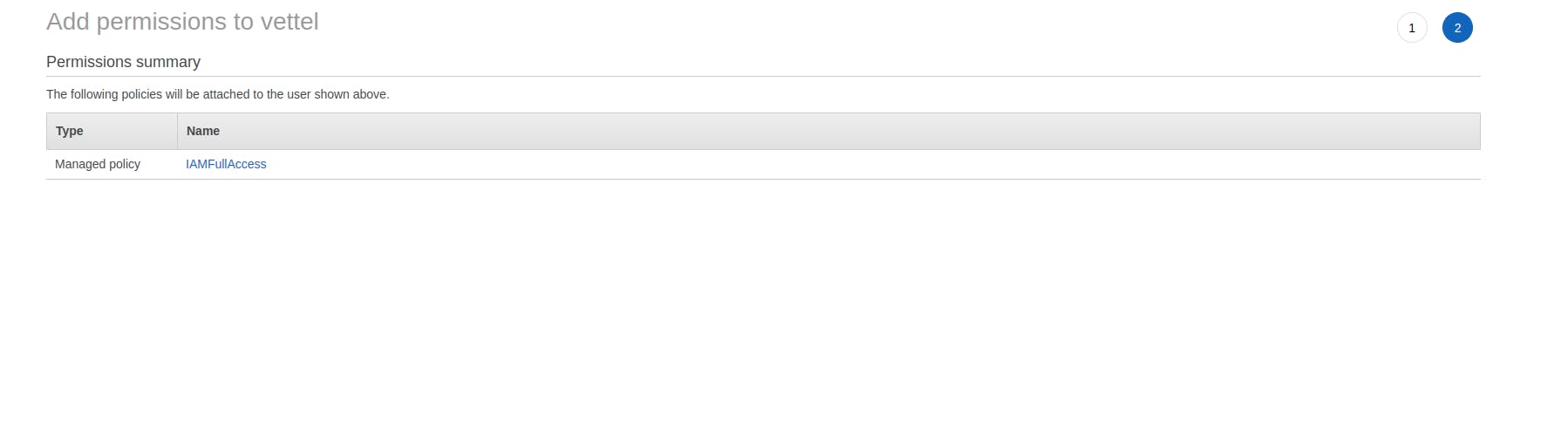
- It would show us the summary of the permissions added.
- On the console you could see that the newly added permissions are added onto the user.
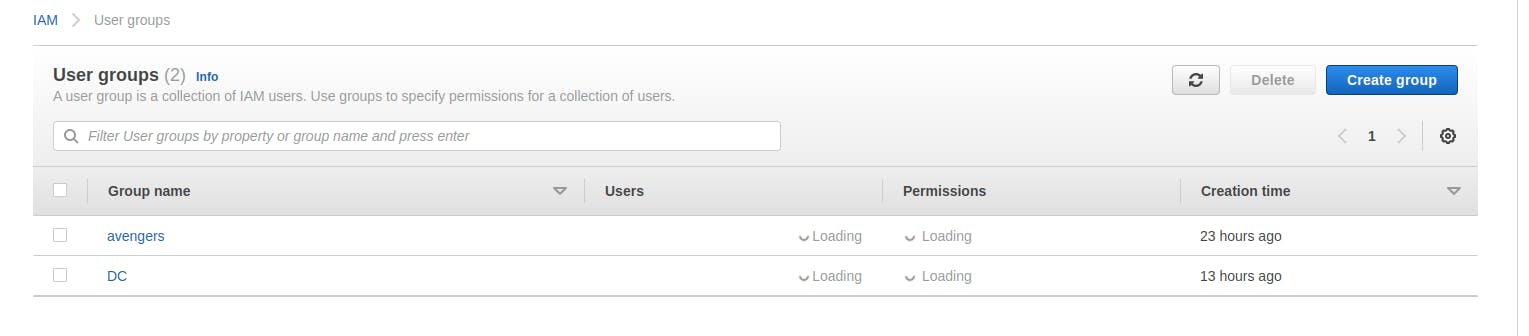
How to add User to certain group ?
Steps to follow
- Click on user Groups from Side Navigation --> Click on Button Create Group
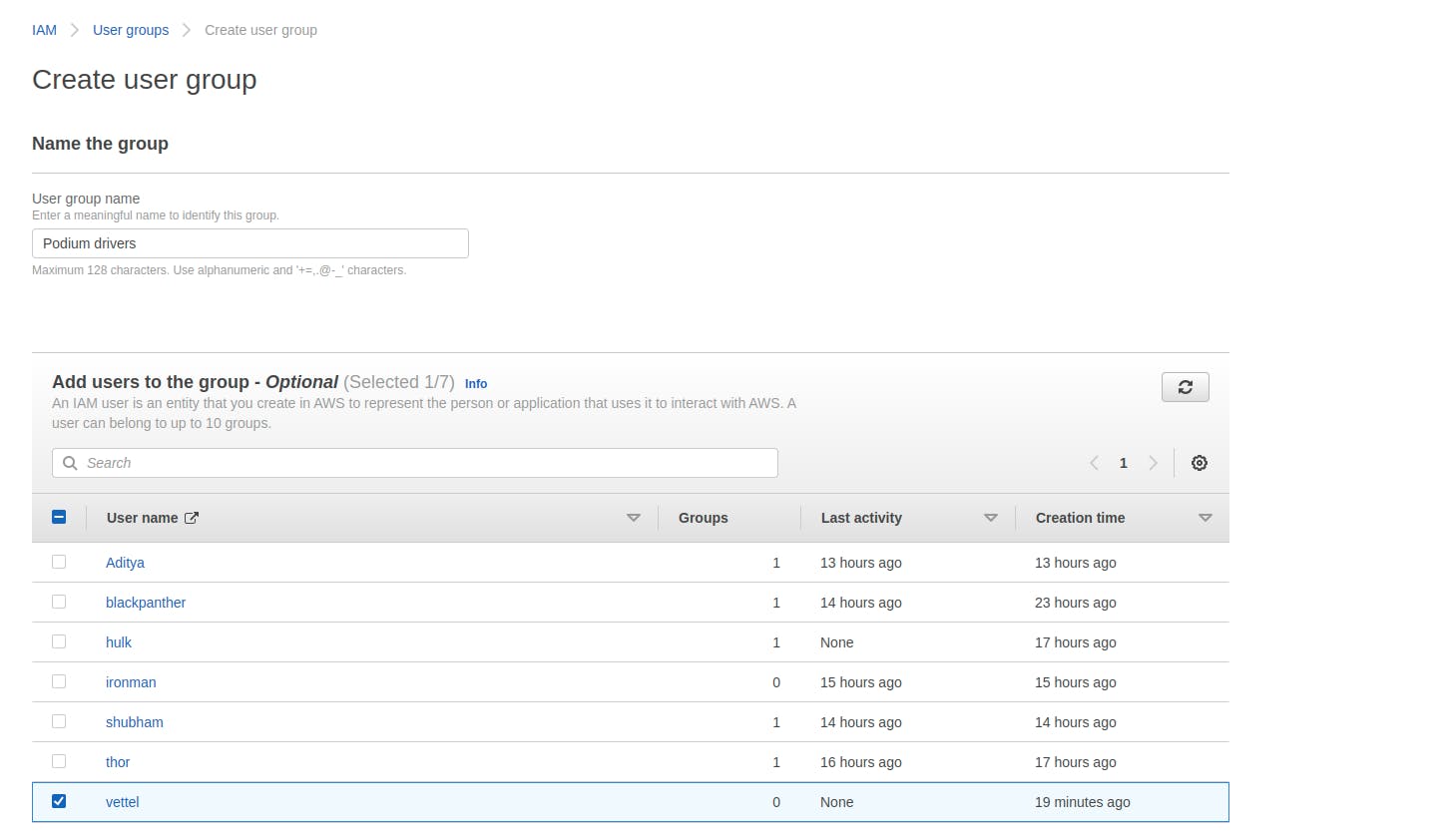
- Name the group and from the below add the users to the group
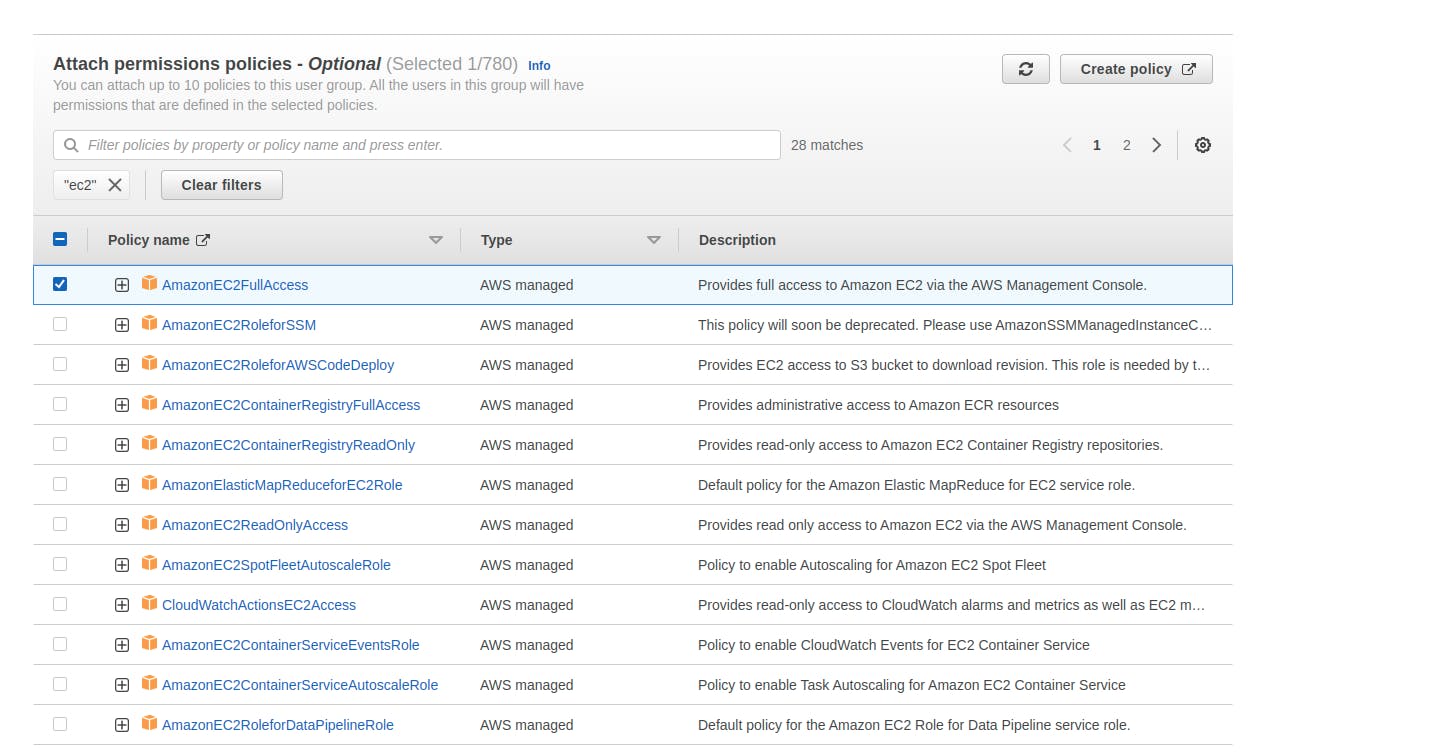
- Below the above options we can attach the permissions policies
- In the User groups the newly added group will be shown
IAM Policies
A policy is an object in AWS that, when associated with an identity or resource, defines their permissions. AWS evaluates these policies when an IAM principal (user or role) makes a request.
The Users and the Groups the policies can be assigned via the ### JSON doc (They have the builders inside the AWS which helps us to write these policies).
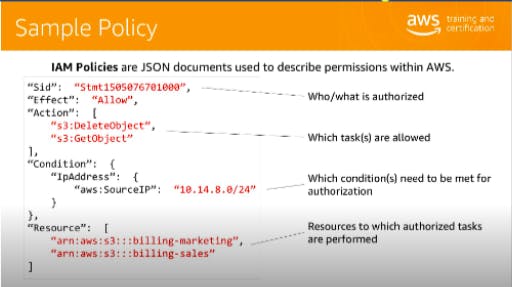
Now if we move onto some of the ### Advance Policies then we can segregate tem into parts like
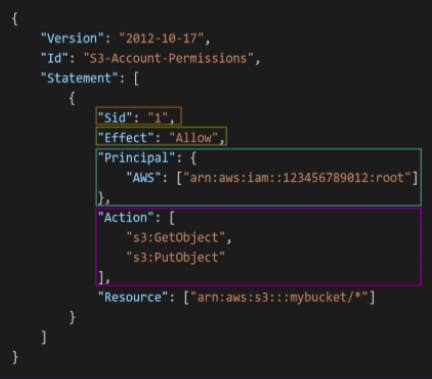
- Version:
It represents the policy language versions
Statement:
- It represents statement for one or more individuals
- Sid : It represents the identifier of the statement
- Effect: It allows or denies the access to the policies.
- Principal: It defines the account/role/user to which the Policy is applied to condense the following it gives us the source of impact.
- Action: It defines us the kind of policies we want to allow or deny to users
- Resource: It is a resource to which the action is applied.
"AWS" : [ "arn:aws:iam::12345566798:root" ]
iam - represents the service which we are using
12345566798 - represents the id of the user
root - by whom the access is given in this case root (Permission can also be given by the groups)
Phew that's quite a Hands-On ! (Worth It !)
I hope this article has received well with all of you guys. It will definitely help you to get on and get started with the AWS Journey and I will definitely try to keep posting often and make sure that you enjoy while learning the things and getting it done.
Till then Stay tuned for the next one. I hope you are having a good day !
Every Feedback is appreciated it will help me to get better and deliver you guys a great content.
